The content of the article:
- 1 What is MD5 used for?
- 1.1 Hash Properties
- 1.2 Independent use of MD5
- 2 How to decrypt MD5 online
- 2.1 MD5 decoding online
What is MD5 used for?
MD5 technology is used as one of the cryptographic methods by which not only integrity is checked various data, but also:
- online keys and passwords are stored;
- web identifiers and digital signatures are created;
- searches for duplicate files and more.
MD5 is widely used for authorization on various sites. Information entered by users is read in the form of prints and stored in the site database. Therefore, even if the attacker and will steal this base, he will not be able to use it directly way. All passwords are encrypted and represented by digests. Next i I will talk about decrypting the MD5 file with online services.
It is in order to avoid falling into the hands of scammers, many data on the network and are transmitted in encrypted form. Information assigned MD5 = (random combination of characters), e.g. MD5 = 214d9a2575bb130ac5f19a8531e6e5f1. This character set (after “=”) called an “MD5 hash”, or checksum is a countable result. This hash serves for checking the transmitted data on integrity.
How does this happen?
- When transmitting an array of information whose integrity is needed control, the original hash is calculated, calculated at using the MD5 algorithm;
- the result is recorded;
- regular or unscheduled inspection compares received checksum from the original;
- the results are the same – there is no cause for concern, if they different, then it speaks of extraneous interference and change data.
Hash Files
Hash properties
A hash function must be able to convert information to various lengths in code consisting of 32 hexadecimal characters. Besides of this, there are several points to protect User from tampering and changes encrypted information:
- if different input data are used, then the results Hash calculi should differ markedly;
- function algorithm must be open in order to be able examine it for cryptographic strength;
- Hash encryption is performed unilaterally, i.e. in no way can you calculate the original information.
The hash function should use minimal computational resources.
Do-it-yourself MD5
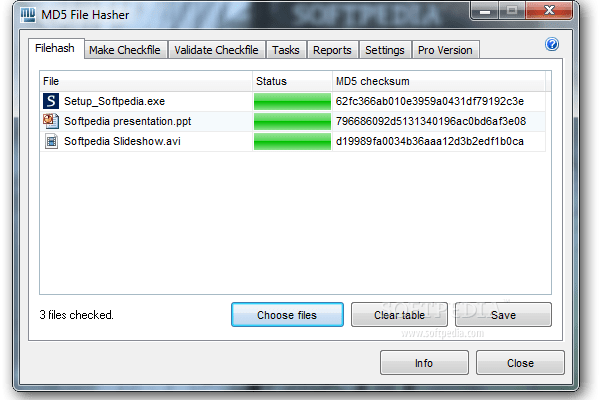
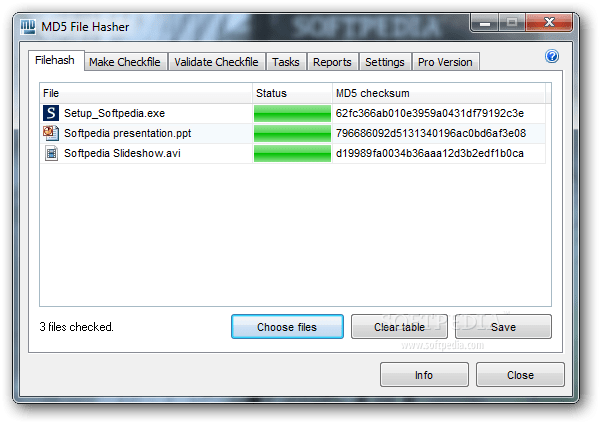
There is one interesting point here – with the help of this functions, each user can independently check for integrity of a file downloaded from the Internet. For this you need use special services, for example, HashTab. Utility downloaded and embedded in the file properties as a separate tabs. With HashTab, you can use several data hashing algorithms, in addition, the service is located in free access for users who use it in personal purposes.
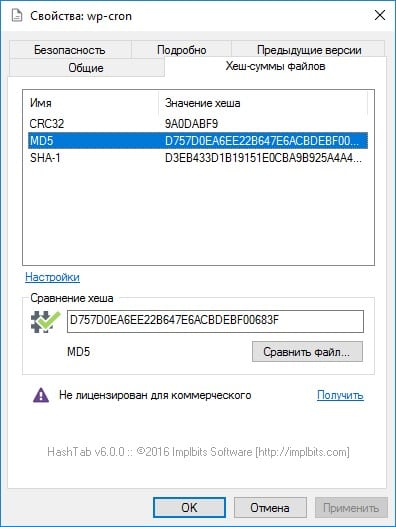
HashTab at work
How to decrypt MD5 online
An arbitrary array of information is converted to a “digest” or “Imprint” of a certain length. Subsequently, when checking the file the resulting code is compared with the original fingerprint and the conclusion is made about data integrity. In general, decrypt a hash code impossible, since it was created so that it could not be hack. Conventional decoding methods in this case are not They work because the information is presented in a slightly different way. Therefore, although this is difficult, it remains to try to pick up the required information, in which special services and programs.
MD5 decoding online
How does the online service used to decode MD5 work? is he has a database that is accessed when decrypting the hash code. For example, the MD5 Decrypter website.
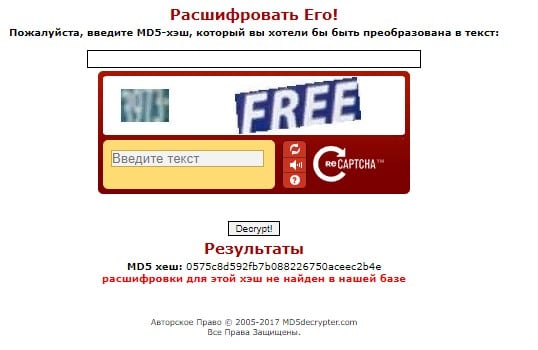
Decryption in the MD5 Decrypter service
In the special field, enter the hash code that we need decrypt, captcha values and click decrypt (“Decrypt!”, if the site has not been translated into Russian). Below will be results: MD5 hash and its decoding, or information that decryption is not in the database.
You can also use the online tool MSurf.ru. The the service allows you to both encode information using MD5, and decrypt the hash code.
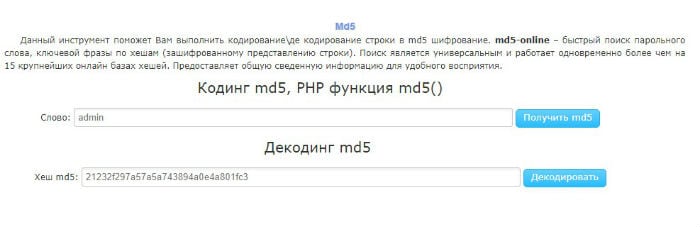
Encode and decode information on MSurf.ru
It is worth noting that the MD5 function is becoming obsolete. Intruders get access to databases and with a certain degree of probability – to encrypted information. Therefore, due to the relative unreliability software developers are advised to use MD5 either in complex with other algorithms, or gradually replace it with more modern SHA.